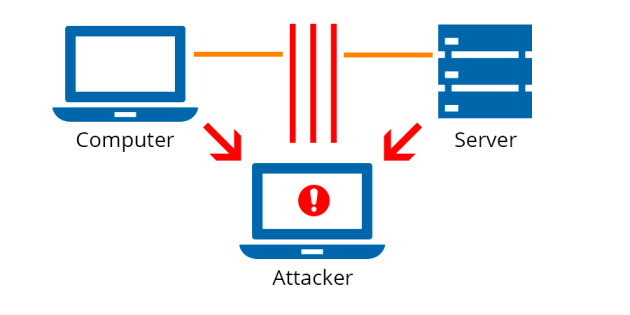
The Man in the Middle Attack (mitm) intercepts communication between two systems in which an unauthorised person monitors and modifies communication between two users. Data is transported from point A (computer) to point B (server/website), for example, and an attacker can get in the way.
They then put up instruments that would “listen in” on communications, intercept data that was expressly targeted as valuable, and record it. The Man in the Middle Attack can occur in any type of online communication, including email, social media, and web browsing.
They can not only listen in on your private talks, but they can also target all of the data on your devices. Man in the Middle Attacks (mitm) are designed to steal personal information such as login credentials, account information, and credit card numbers. This data can be altered during transmission to try to fool the end user into disclosing sensitive information like login passwords.
The two initial parties appear to converse normally during the Man in the Middle Attack(mitm) process. The message sender is unaware that the receiver is an unknown attacker who is attempting to access or modify the message before retransmitting it.
As a result, the Man in the Middle Attacker has complete control over the communication.
A passive assault in which an attacker makes free, malicious WiFi hotspots available to the public is the most prevalent (and easiest) form of Man in the Middle Attack. They aren’t password secured and are usually titled in a way that matches to their location. When a victim connects to one of these hotspots, the attacker has complete access to any online data exchange.
Because the HTTP protocol and data transit are both ASCII-based, the Man in the Middle Attack is quite effective. It is possible to watch an interview within the HTTP protocol as well as the data transferred from the Man in the Middle Attack. Due to its ease of implementation, a newer form of the Man in the Middle Attack is gaining favour among cybercriminals.
An attacker needs a technique to inject malware into the computer, which will then install itself into the browser without the users’ awareness and capture the data transmitted between the victim and specific targeted websites, such as financial institutions, which are coded into the malware. When the malware has collected all of the data it was programmed to capture, it sends it back to the attacker.
Connection Susceptible to Man in the Middle Attack
- Financial sites between login and authentication
- Connections meant to be secured by public or private keys
- IP spoofing
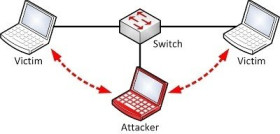
- ARP spoofing
- Sidejacking
- Sniffing
- DNS spoofing, also known as DNS cache poisoning
- Other sites that require logins where there is something to be gained by having access
How to Prevent MITM
- Wi-Fi connections that aren’t password protected should be avoided.
- Make sure the URL bar of the websites you visit always says “HTTPS.”
- Be aware of phishing emails from attackers requesting that you change your password or other login information.
- Instead of clicking on the email’s link, manually type the address of the website in question into your browser’s URL bar and proceed from there.
- Make sure your home network is protected.
- Keeping an eye out for browser indications that a website is insecure.
- When not in use, immediately log out of a secure application.
- When completing sensitive transactions, avoid using public networks (e.g., coffee shops, hotels).