TECHNOLOGY
What are VoIP Attacks and conventions utilized by VoIP
Because of the growing ubiquity of IP communication administrations, there is genuine concern about VoIP security. With potential security threats...
Read moreWhat is SS7 Attacks (Signaling System 7)
SS7 Attacks is a worldwide broadcast communications standard that specifies how components in an open switched telephone network (PSTN) trade...
Read moreWhat is Public Switched Telephone Network (PSTN)
The Public Switched Telephone Network (PSTN) is a system of interconnected voice-oriented public telephone networks built on copper cables delivering...
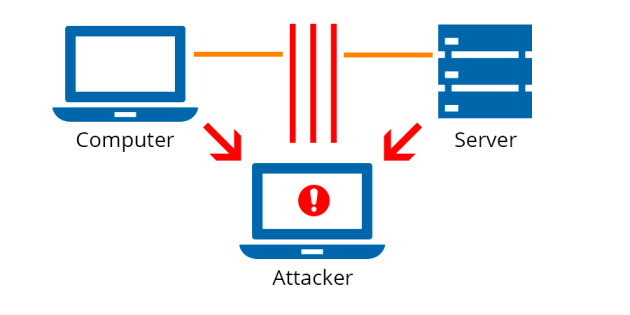
Read moreWhat is Man in the Middle Attack and How to Prevent it
The Man in the Middle Attack (mitm) intercepts communication between two systems in which an unauthorised person monitors and modifies...
Read moreWhat is Motherboard and What was the first motherboard
In a computer, the motherboard is the main circuit board. Its purpose is to link all of the components of...
Read moreWhat is zombie computer and its Symptoms
A zombie computer or network is a group of infected computers or hosts that are linked to the Internet and...
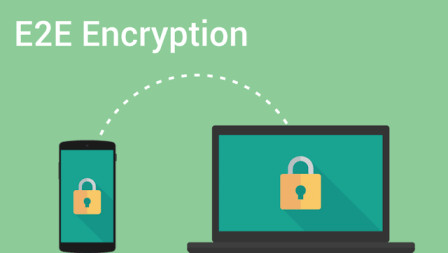
Read moreWhat is End-to-end encryption and how It works
End-to-end encryption (E2E) is a secure communication mechanism that protects encrypted data as it travels from source to destination. Only...
Read moreWhat is Biometric authentication and its Types
Biometric authentication is a human identity verification security procedure that utilises biological input, such as fingerprints, palm or finger vein...
Read moreWhat is Backdoor & how to clean your infected system
A backdoor is a method of gaining access to a computer system or encrypted data by circumventing a system security...
Read moreWhat is Facial Recognition How does it work
Facial recognition is a biometric software tool that can uniquely identify or verify an individual by comparing and analysing mathematical...
Read moreRadical © Copyright 2021, All Rights Reserved