Remove Spyware From Mac:
One of the sneakiest types of malware is spyware or surveillance software. And yes, Macs can be infected. Keep hackers and other unsavory individuals from spying on you. Get Mac spyware eradication right away. The quickest way to get spyware off your Mac is to manually delete it or use a program like AVG AntiVirus.
Confirm if Your Mac Has Been Infected before Removing Spyware from Mac:
It’s critical to realize that spyware can be fooled for legitimate software quite simply in contrast to other types of malware. The majority of Mac spyware won’t change any operations, whereas most malware will legitimately change your system and settings. Instead, it operates like any other program and observes and logs all activity on the target Mac. Because the information gathered can be easily transferred and exploited by a third party for nefarious purposes, this eventually jeopardizes your security. However, even though it might appear challenging, spyware removal for Mac is not insurmountable. There are straightforward methods that work.
Here are a few easy steps:
- A system scan will make it simple for you to do this by allowing you to see which apps are currently operating.
- it’s crucial to remember that not all spyware will be simple to find.
- Use the spyware detectors that are readily available to identify any unusual activity to make sure you don’t miss out.
Can Macs get spyware?
The idea that Macs are immune to malware and viruses has long been fiction, but it has to be dispelled. Although Apple devices come with some useful built-in security safeguards, Macs are nevertheless prone to all types of malware, with spyware being one of the most pervasive and dangerous types on the platform.
What is spyware?
Spyware is harmful software that infiltrates your computer and then ingests personal data, including keystrokes, financial information, keystroke patterns, web browsing history, and even camera photographs.
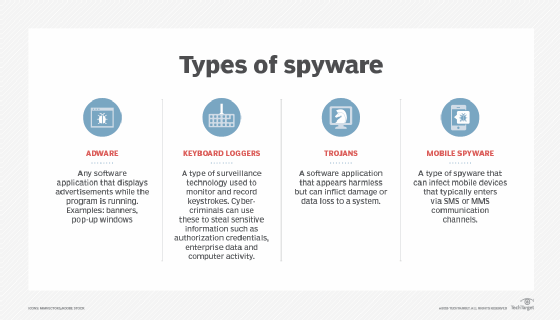
There are four main types of spyware:
Keyloggers:
A piece of software known as a keylogger records key presses and is typically installed without the user’s knowledge or consent. By doing that, the keylogger can access sensitive data including credit card numbers, usernames, and passwords as well as other personal information.
All forms of malware share one characteristic with spyware: it acts without your knowledge or agreement.
It can therefore covertly access your:
- Activity on the browser and location
- Addresses and content
- Chats and emails
- keystrokes and the display
- usernames and passwords
- Webcam, printer, and microphone
- such as financial information,
Trojans:
Trojans are malicious files that impersonate trustworthy ones, such as software updates or movies, to trick users into downloading them. They will have access to your data after you do that, which could damage your Mac.
Adware:
The most prevalent kind of spyware is undoubtedly adware. It’s also the most noticeable because pop-up windows or advertisements are displayed using spyware’s data. Although it is extremely uncomfortable and frustrating, there is little chance that it will harm you or your Mac.
Cookie trackers:
In that they track your web searches and browsing patterns, cookie trackers are comparable to adware. The hacker can then utilize the information however they see fit, such as to display adware.
How to find spyware on Mac?
The solution to that query is observation and system monitoring, just as how you would know if you became ill. With apparent performance differences, spyware on your Mac is simple to find. Spyware-infected Macs run slower, consume batteries more quickly, and frequently overheat. Applications are slow and unresponsive; bandwidth usage is out of control; browsers are loaded with advertisements, etc.
If you’ve observed any of these issues, see what’s using up all of your CPU. For that, utilize App Tamer. It is a cutting-edge Mac CPU monitoring solution. You may forcefully slow down any software using App Tamer by monitoring its processes and applying limits to prevent system paralysis.
Here’s how you can set limits in App Tamer:
- Start App Tamer
- Then select the program you wish to restrict.
- “Slow down this program if it uses more than:” should be checked.
- Enter the required percent.
Are there any free spyware removal tools?
You may be asking at this point if any free Mac spyware detection tools are available. There are, but you should use them with extreme caution.
You must grant these programs almost total access to your Mac for them to properly check for malware. How do you know they don’t include any spyware themselves if they are free?
For all your malware needs, we advise sticking with well-known and trusted scanners like CleanMyMac X. Additionally, you may upgrade your Mac with Step Two to allow 2FA codes, App Tamer to control CPU processes, and ClearVPN to obfuscate your web traffic.
Best of all, Setapp, a platform with more than 210 top-rated Mac apps, is offering a trial that allows you to use CleanMyMac X, App Tamer, ClearVPN, and Step Two for free seven days. You can immediately discover which apps you’ve been missing out on by downloading the whole Setapp library for free now.
How does spyware work on an iPhone?
Spyware, also known as stalkerware, sets up shop on your device, observes your behavior, and sends your information to third parties without your permission. Sometimes the spyware is put on someone else’s device by a controlling parent or lover who wants to snoop on them.
Spyware can monitor your location, movies, images, text messages, and call history on your phone. Even worse, it can activate your microphone or camera, record calls, grab pictures, and monitor your activity on apps like WhatsApp or Snapchat.
When it comes to iPhone spyware, it comes in a few different forms. For instance:
Spyware of the common or garden variety. A program tracks your activities after covertly installing itself on your smartphone. Typically, it is operated remotely by cybercriminals who log in to the app or website that triggers the spyware using a different device.
Malware attacks against iCloud. In this instance, hackers discover your iCloud login information. They can monitor everything you do on your smartphone as a result.
Masque assaults A spyware application poses as an update to a trustworthy app you’ve previously loaded on your smartphone in this kind of intrusion.
Spyware, irrespective of variety, operates covertly. This indicates that you won’t get any phone notifications about it. Not even on your home screen will you locate it. Fortunately, spyware can still be quickly found on your device and removed from it permanently. How? Read on.