TECHNOLOGY
How to Generate AI Images Using Midjourney
A lot of time is spent on the internet trying to figure out how to tell AIs best what to...
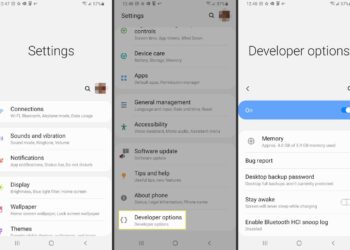
Read moreHow to Enable Developer Options on Android Phones
You can change a lot of things about an Android phone, but you can always go further by using developer...
Read moreRemoving an Account from Google Smart Lock: A Quick Guide
The Google Smart Lock is a cool piece of tech that works on many Google and Android devices. When turned...
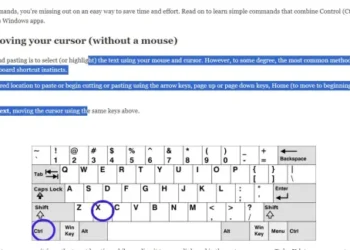
Read moreHow to Use Cut, Copy, and Paste: Windows Keyboard Shortcuts Guide
Do you hate having to constantly right-click in order to use basic editing tools like cut, copy, and paste? While...
Read moreWhat is Cybersecurity and Types of Cybersecurity threats
Cybersecurity is the process of safeguarding internet-connected systems, networks, software, data, hardware, and programmes from cyberattacks. Cybersecurity is a term...
Read moreHow to Capture Screenshots on a Windows PC or Laptop
Taking screenshots is a great way to save pictures on your desktop, but if this is your first time doing...
Read moreHow to Enable and Disable Safe Mode on Your Android Phone
Safe mode helps computer developers debug, but you can enable it on your Android phone. It can unlock critical functions...
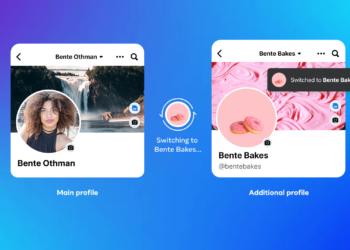
Read moreHow to Create Multiple Profiles on Your Facebook Account
There are certain rules about how Facebook (and, by extension, Meta) users can make accounts and use their platform. Facebook...
Read moreHamraaz Login: How to Access Your Account Online
The Indian Army created Hamraaz login as a digital tool to offer different services to its employees. It's a mobile...
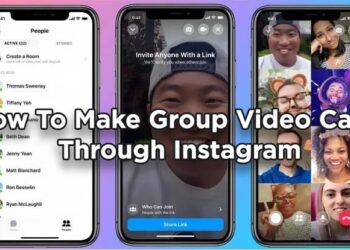
Read moreHow to Start and Manage Video Calls on Instagram: A Complete Guide
Instagram is one of the most popular social media platforms in the world, with over one billion active users. One...
Read moreRadical © Copyright 2021, All Rights Reserved