As digital transformation accelerates across every industry, the demand for robust internet security continues to soar. The global cybersecurity market, valued at $160 billion, is projected to reach $273 billion by 2028, according to Statista. This explosive growth reflects a pressing need for advanced cybersecurity solutions as cyber threats become increasingly sophisticated.
From ransomware to data breaches, businesses and individuals alike are seeking reliable cybersecurity providers to protect sensitive information. With so many options available, choosing the right cybersecurity company can be overwhelming.
To help you make an informed decision, we’ve compiled a list of the top cybersecurity companies leading the industry in 2025. These providers offer innovative, comprehensive, and trusted security solutions to safeguard your digital world.
What Are Cybersecurity Service Providers?
Cybersecurity service providers offer a wide range of tools and services designed to protect digital assets from unauthorized access, cyberattacks, data leaks, and other threats. These solutions include endpoint protection, threat intelligence, vulnerability management, firewalls, antivirus software, and cloud security platforms.
Whether you’re a business owner or an individual looking to secure your online activities, these cybersecurity companies can deliver the protection you need.
Best 10 Cyber Security Companies
1: Tenable
Key Services:
-
Web application security
-
Cloud security
-
IoT protection
-
Vulnerability scanning
-
Configuration auditing
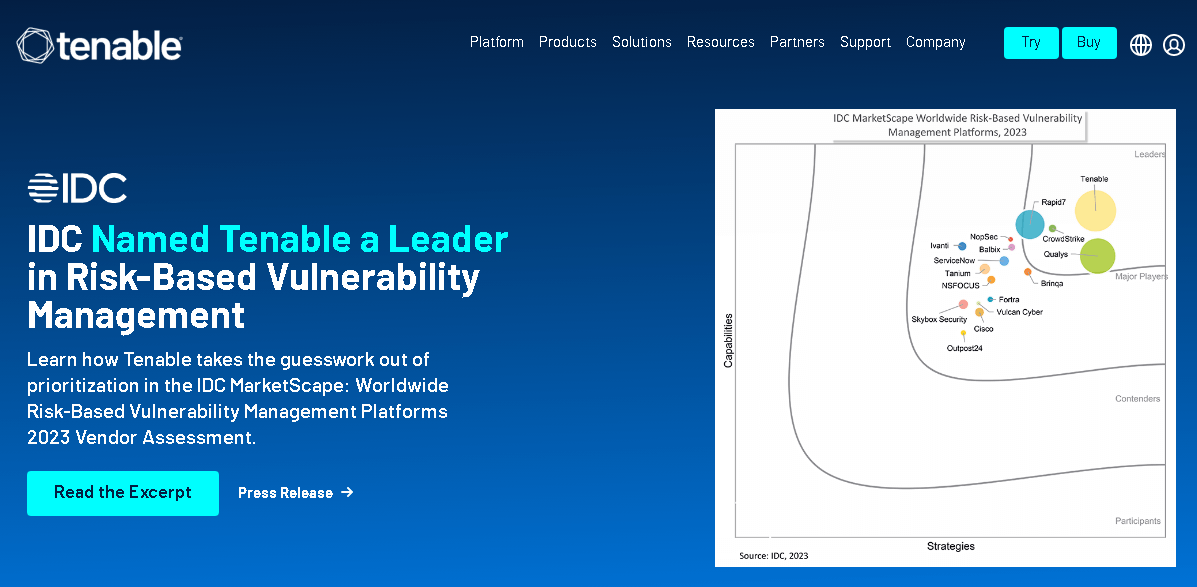
Tenable is a well-known cybersecurity provider of managed security services. Their products enable consumers to understand and minimize cybersecurity risks. Additionally, Tenable provides a Web App Scanning function for contemporary web apps, enabling security teams to learn about potential threats.
Web application security, cyber exposure, container security, cloud security, IoT security, vulnerability management, network monitoring, configuration auditing, compliance, vulnerability auditing and scanning, log management and analysis, and more are among their services.
Visit Website: Tenable
2: Astra Security
Key Services:
-
Network security
-
Malware protection
-
Penetration testing
-
Web application firewall
The leading supplier of VAPT security services for networks, cloud, APIs, and web and mobile apps is Astra Security. Its thorough vulnerability and malware detection enables quick fixes for any malware or vulnerabilities discovered.
To provide optimal security for your cloud environment, it also offers top-notch firewalls, ongoing vulnerability scanning, and recurring penetration tests.
Visit Website: Astra
3: Iboss
Key Services:
-
Secure web gateway
-
Malware detection
-
Data loss prevention (DLP)
-
CASB integration
A global provider of cloud security services, Iboss gives businesses and staff members safe global access to the internet. It offers excellent third-party integrations as well for cloud-native security features.
It offers features including data loss prevention, CASBs, malware detection, and the ability to block 4 billion threats every day while handling 150 transactions.
Visit Website: Iboss
4: Avast
Key Services:
-
Antivirus software
-
Ransomware protection
-
VPN and privacy tools
-
Automatic patch management
Avast is a well-known cybersecurity provider with a wide range of services available at reasonable prices. These services, which are available for PCs running Mac, Android, and iOS operating systems, include antivirus, ransomware, identity theft, and data protection.
With the assistance of knowledgeable technical specialists, it offers clients round-the-clock IT support in addition to automatic patch management services. With Avast, users can safeguard their network connections when utilizing public wifi networks and enjoy unlimited VPN services.
Visit Website: Avast
5: CrowdStrike
Key Services:
-
Endpoint protection
-
Threat intelligence
-
Managed threat hunting
-
Cloud-native security
Well-known IT business CrowdStrike specializes on cloud-native endpoint security, a subset of cybersecurity. Their state-of-the-art Falcon platform successfully thwarts endpoint threats regardless of the network connection, providing immediate insight and strong protection across enterprise environments.
Threat intelligence, next-generation antivirus, endpoint detection, response, and managed hunting services are all included in CrowdStrike’s extensive service package. CrowdStrike’s strategy integrates cutting-edge technology, intelligence-driven insights, and quick reaction capabilities with the unwavering goal of preventing breaches.
Visit Website: CrowdStrike
6: Zscaler
Key Services:
-
Zero trust network access
-
Secure web gateway
-
SaaS security
-
Threat detection and analytics
Zscaler, another top cybersecurity service, gives customers control over a strict zero-trust security posture, facilitating easy navigation and enhancing security posture security.
Distributed cloud-based security, independent of client location, for email, mobile, and web applications. In order to give corrective actions and secure access to the SaaS application with notifications for any abnormalities or threats detected, it assists in identifying SaaS application misconfigurations and improper access authentication.
Visit Website: Zscaler
7: Cisco
Key Services:
-
Network security
-
Email and endpoint protection
-
VPN and firewall solutions
-
Identity and access management
Cisco is a top supplier of cyber security solutions, including VPN to safeguard staff members’ internet connections, sophisticated malware protection, and next-generation firewalls and intrusion prevention.
Security management, email security, and endpoint security are further services. These services, when combined with Cisco’s Identity and Access Management, provide a wide range of highly favoured goods and services.
Visit Website: Cisco
8: Microsoft
Key Services:
-
Azure cloud security
-
Threat intelligence
-
Identity and access management
-
Data protection
Identity and access management, cloud security, DDoS prevention, threat and information protection, and vulnerability management are just a few of the security features that Microsoft provides.
Microsoft offers a variety of technologies for Azure cloud security services, including Microsoft Sentinel, Azure Key Vault, Active Directory for identity and access management, and more.
Visit Website: Microsoft
9: Trellix
Key Services:
-
Incident response
-
Endpoint and network security
-
Threat detection
-
Email protection
Global cybersecurity leader Trellix offers cutting-edge threat intelligence and security solutions. Trellix is dedicated to staying ahead of the curve in the constantly changing cybersecurity field by placing a significant emphasis on innovation. Threat intelligence, incident response, network, email, and endpoint security are all included in the company’s extensive service package.
Trellix’s solutions are made to identify and stop cyber threats before they have a chance to do a lot of harm, protecting the confidentiality and integrity of their customer’s data.
Visit Website: Trellix
10: Trend Micro
Key Services:
-
Hybrid cloud security
-
Endpoint protection
-
Network defense
-
Email security
The leading cybersecurity company in the world, Trend Micro creates cutting-edge security solutions for individuals, organizations, and governments.
The business offers layered security for networks, endpoints, cloud environments, and data centres. Trend Micro offers solutions that defend against a variety of attacks, including as spear phishing, ransomware, and advanced persistent threats. Ensuring global security for digital information exchange is their aim.
Visit Website: Trend Micro
Final Thoughts
With cyber threats growing more sophisticated each day, partnering with a reliable cybersecurity provider is essential. These top cybersecurity companies in 2025 offer cutting-edge technology and expert support to keep your data and systems secure.
Whether you’re looking for endpoint protection, cloud security, or vulnerability management, the providers on this list offer comprehensive solutions tailored to your needs. Explore their platforms and choose the one that aligns with your security goals.